Differences in advance data extraction methods from the mobile phone
The paper will reflect the different tool classification used for mobile forensics. Understanding the different level allows individual to know which tools will be most suitable for mobile forensics. We will also need to know the pros and cons of each level. Understanding all these will result in the most suitable tools being used.
The chief goal of tool classifications is mainly to enhance examiner with fundamental skills to compared and classify extraction technique of the different tools easily. Tool classification has been demonstrated in Figure 1 below. Since a pyramid is usually traversed from the bottom, level to top level, that is, from level 1 to level 5, techniques utilized in the acquisitions turn more invasive, expensive, technical, and time-consuming.
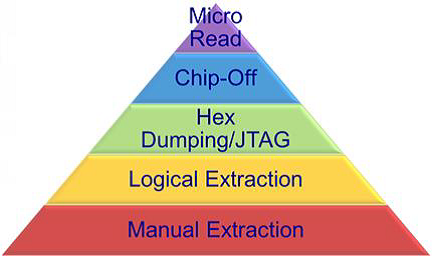
Figure 1
The Manual Extraction techniques (Level 1), comprises merely of recording information from the mobile phone screen while utilizing user interface.
Logical Extraction methods or the Level 2 are usually utilized regularly and slightly technical, calling for the beginner-level or new user training.
The Hex Dumping or the JTAG Extraction techniques (Level 3), a working “physical acquisition” of the mobile memory in situ, mostly calls for advanced or sophisticated training.
Chip-Off methods (Level 4) comprises of removal of the physical memory from mobile phone to the extraction of data, which necessitates or calls for extensive or broad range training in the electronic engineering as well as file system forensics.
Micro Read methods (Level 5) comprises of utilization of high-powered microscope in viewing the physical state of the gates. These methods are the most invasive, sophisticated, technical, expensive, and time-consuming of all the methodologies.
Understanding the Pros and Cons
Based on https://articles.forensicfocus.com/2014/10/28/extracting-data-from-dump-of-mobile-devices-running-android-operating-system/, there exist different benefits and drawbacks for carrying out extraction forms at every layer.
For instance, the hex dumping permits the deleted objects as well as any data remnants in existence to be assessed (such as the in unallocated file system space of the unallocated memory), which would otherwise be inaccessible via the utilization of the logical acquisition techniques.
Nonetheless, extracted device figures call for parsing, decoding, and decryption. The logical acquisition techniques, though a bit limited than the Hex Dumping or the JTAG techniques, have benefits in that these system data arrangements are at higher levels of the abstractions and they are quite more comfortable for the tool in rendering and extracting.
The variances are as a result of underlying diversion in between the memory as viewed by the procedure through operating system facilities, versus the memory as viewed in the raw form by processors or other hardware elements.
From the broader range of situations such as the form of data required, available tools, urgency, time available and so forth, the examiner or assessor might choose a particular level to start their assessment. It is significant to understand that once the level is utilized, other levels might be impossible. For instance, after conducting the chip-off, lower level, might not be at any point look physically possible.
The forensic assessor ought to be aware of or informed of such problems and carry out the suitable level of the extraction correspond with some of their experiences and training. With every technique, the data might always be modified or destroyed in case a specific procedure or tool is improperly used. The risk of destruction and alterations rises in line with specific levels.
Therefore, appropriate mentoring and training are crucial in accessing the highest rate of success for the analysis and extraction of data in mobile phones.
Manual Extraction
The manual extraction technique of the data comprises of viewing data components contained in the mobile phones. Some of the content contained on LCD screen calls for manual manipulation of the keyboard, touchscreen or buttons in viewing contents on the mobile phones. The information retrieved might be reported through external cameras.
Following up on http://www.foodqualitynews.com/Lab-Technology/Analytik-Jena-tech-now-available-for-manual-extraction, at this extraction level, it is impossible to recover deleted information. Some tools have been developed to provide the capacity of categorizing and documenting information reported more swiftly.
However, in case there is a relatively massive amount of the information or data, manual extraction could be time-consuming or wasting, and data contained within the mobile device might be inadvertently overwritten, modified or deleted due to assessment. The manual extractions turn out to be increasingly hectic and perhaps unattainable whenever encountering missing or broken LCD screen or missing or damaged keyboard interface.
In addition, many obstacles take place whenever the mobile device is sometimes configured in displaying languages unknown to an assessor, which might result in difficulties in fruitful menu navigation.
Logical Extraction
Retrieved from http://www.cellebrite.com/Pages/logical-extraction-of-mobile-data, Logical extraction of data is performed through the device’s designated API (Application Programming Interface), available from the device vendor. The connectivity in between the mobile phone and forensic workplace is usually accomplished with a connection utilizing either wired such as RS-232 or USB or wireless such as WiFi, Bluetooth or IrDA) connections. Generally, the assessor must be fully aware of some of the issues linked with a selection of particular connectivity techniques since diverse connection forms as well as related protocols might leads to data or information being modified or diverse forms or types of the information being extracted.
Upon the connection, the UFED is said to load significant API in the mobile phones. The UFED later make the read-only API calls in requesting the relevant information from devices. Later devices provide replies to the valid or appropriate requests in extracting designated content from operating systems utilizing the relevant set of the commands. This implies that the data extraction components communicated with the mobile phone’s operating system requesting relevant information from this system. Such procedure enhances acquisition of relevant or most live data within the mobile phone, in a readable format as well as in forensically sound mean.
The form of the data comprises of call logs, phone details, passwords, phonebook entries, videos, apps data from the Android devices, SMS, audio files, SIM deleted call logs, images and so forth. In most scenarios, the logical extraction is impossible for the locked devices.
Additionally, logical extraction technique is technically quicker and more comfortable for the tool to operate, since it is mostly limited to the amount of the data it could extract, unlike the physical extraction techniques.
Within a specific market, the Cellebrite’s tools usually enhance logical extraction from the broadest range of the devices, memory cards, phones, portable GPS devices as well as tablets produced with the Chinese chipsets.
Hex Dumping as well as the JTAG
The Hex Dumping as well as the JTAG extraction techniques usually afford forensic assessors a more direct admittance to raw information recorded within the memory. The chief problem with such extraction technique is the capacity of the provided tool in decoding and parsing captured data or information. In addition, provision of logical views of the file system as well as reporting on the other information remnants externally from the file system to forensic assessor might be challenging. For instance, all the information in a provided flash memory might not necessarily be acquired since numerous tools like flasher boxes might just be capable of extracting particular sections of the memory. The techniques utilized at such level need connectivity such as WIFI or cable between the mobile phone and forensic workplace.
Bases on https://articles.forensicfocus.com/2014/10/28/extracting-data-from-dump-of-mobile-devices-running-android-operating-system/, the Hex Dumping approach is a more frequently utilized technique at such level. Such comprises of uploading modified bootloaders in a protected area of the memory such as the RAM on mobile phones. The upload procedure is usually achieved by connecting the mobile phone’s data port to the flasher box, and later flasher box is connected to the forensic workplace. Numerous commands are then sent from flasher box to mobile phone in order to place the device in diagnostic mode. After it is turned in the diagnostic mode, flasher box then captures all of the memory and later send the information gathered to the forensic workplace through similar communications line utilized for upload. Some of the flasher boxes usually function in this manner, or they might utilize a proprietary edge for the memory extractions. Uncommon scenarios exist where the extractions could be achieved through WiFi techniques.
A good number of the producers are said to support JTAG standards that describes common test interface for memory, processor as well as the other semiconductors chips. The forensic assessors could communicate with the JTAG-compliant element by using some particular purpose individual programmer component in probing the defined test points such as the Wil05. Generally, the JTAG testing unit could be utilized in requesting memory addresses from JTAG-compliant constituent and accepting a role for rendition and storage.
The JTAG offers the specialists other avenues for the imaging devices which are mostly locked or the devices which might have minor damages and could not be appropriately interfaced otherwise. Such technique comprises of attaching the cable from the workplace to mobile phone’s JTAG interface as well as accessing the memory through phone’s microprocessor in producing images. The JTAG extractions vary from the Hex Dumping where it is usually invasive as the access to connection regularly need assessors to dismantle most or some of the devices in obtaining admittance in establishing wiring connections.
The flasher boxes are usually small components mostly designed with the aim of upgrading or servicing the mobile phones. The material acquisitions usually call for the use of the flasher boxes in facilitating the extraction of the data. These flasher boxes assist forensic assessors by communicating clearly with mobile phones utilizing the diagnostic protocol in communicating with memory chips. Such communication might make use of the mobile phone’s operating system or might bypass it together and communicate to a memory chip that is Jon10. The flasher boxes are usually accompanied by the software in order to simplify data extraction working in line with hardware. Numerous flasher box packages offer added responsibility of recovering the passwords from mobile memory as they do in most configurations. Though the acquisition technique varies in between the flasher boxes, the general procedure is utilized.
Some of the drawbacks of using the flasher boxes comprise of:
- Rebooting of devices is regularly needed to start the extraction; this might result in authentication mechanisms in activating prevention of further analysis.
- Numerous flasher boxes retrieved data within encrypted format necessitating assessor to use either the software produced by the in decrypting data or might need reverse engineering data encryption scheme.
- A good number of the mobile models fail to offer acquisition of whole memory range in a provided mobile phone. Only particular ranges might be availed for specific mobile phones.
- Flasher box software usually has numerous buttons with almost similar names. Such confusion might lead experienced assessor pressing wrong or erasing the contents from the phone rather than dumping their memory chip.
- The absence of proper documentation on the utilization of flasher boxes is most common. The extraction techniques or approaches are regularly shared on the forums which are mostly supported by vendors and are moderated by most seasoned users. Therefore, caution ought to be undertaken whenever advice is offered since not all data offered are accurate.
- The forensic utilization: almost all the flasher box models were not necessarily designed with forensic utilizations as all its projected purpose. The assessor should be proficient in the of the flasher boxes and ought to comprehend appropriate function and use of the flasher box.
- In spite of all the aforementioned limitations, utilization of the flasher box models is a crucial option for numerous forensic scenarios. Appropriate training, understanding, experience how tools function is crucial.
A broad range of the technical professionals as well as appropriate training is needed for analyzing and extracting the binary images with such techniques, comprising of connecting and locating to the JTAG ports, creating some customized boot-loaders as well as recreating the file systems.
Chip-Off
Based on https://securitycommunity.tcs.com/infosecsoapbox/articles/2015/11/04/mobile-forensics-data-acquisition-methods, the Chip-Off techniques are described as the acquisition of the data or information directly from the mobile phone’s flash memory. Such extraction calls for physical deletion of the flash memory.
The Chip-Off offers the assessors with a capacity of creating binary images of the detached chip. In offering assessor with information or data in adjoining dualistic format files, the wearing-leveling algorithm should be the converse engineered.
Once comprehensively complete, binary images might be examined. Such form of the acquisition is usually closely linked with the physical imaging as the hard disk drive as in the traditional digital forensics. Comprehensive training is necessary to conduct extractions at such level successfully. The Chip-Off extractions are usually challenging on the basis of the full range of the chip forms, a myriad of the raw data forms, and risk of the causing physical impairment to chip during extraction procedures. As a result of complexities linked with the Chip-Off, the JTAG extraction is relatively more common.
Micro Read
The Micro Read comprises of recording of physical observation of gates on NOR or NAND chip with the utilization of electron microscope. As a result of extreme technicalities which are involved while carrying out the Micro Read, such level of the acquisition could just be tried for relatively higher profile scenarios equal to the national security crisis once all the other acquisition methods are drained. At this level, the successful acquisition would call for the team of professionals, an in-depth comprehension of the proprietary data, time and proper equipment. There is hardly any public law enforcement body in the US conducting acquisition at such level. Presently, no Micro Read tools are commercially available.
Author: Tan Kian Hua, Ph.D. student at LIGS University
Bibliography
Gerber, M. and von Solms, R (2005). “Management of risk in the information age.”
Johnston, A.C. & Warkentin, M., 2010. Fear Appeals and Information Security Behaviors: An Empirical Study.
NIST. (2009). “Recommended Security Controls for Federal Information Systems and Organizations.”
Shedden, P., Ruighaver, A.B., Ahmad, A., (2006) Risk Management Standards ‐ The Perception of Ease of Use.
Tipton HF, Krause M. Information security management handbook. Auerbach Publications; 2007.



