
How Virtual Local Area Network (VLAN) Technology Helps Small Business and Organization Cut Costs and Improve Network Performance in the Right Enviroment
In this article, we’re investigating how VLAN technology can be benefits to small business company and organization in general through a variety operational scenario. How VLAN technology can help small busines company and organization saving cost.
Author: Minh Nguyen D.
Introduction
In this article, we’re investigating how VLAN technology can be benefits to small business company and organization in general through a variety operational scenario. How VLAN technology can help small bussines company and organization saving cost.
Our objective that outlines in this article is helping the small business company and organization in general to understand the benefits and the concept of this new technology that was introduced in this article called Virtual Local Area Network (VLAN) in order to help them reduce their capital costs for their baseband diversity project network integration. We’re looking for ways to reduce the capital costs as much as possible for a baseband diversity integration project as demonstrated in multiple operational scenarios. The determination would be can we use the LAN technology vs VLAN technology to support the baseband integration project? Does it feasible to implement VLAN ? what would be the benefits and how this technology can be used to add benefits into the baseband integration project?
Technical Background
What is the baseband diversity integration project in a nutshell?
Virtual Spectrum Aggregator/Virtual Spectrum Manager (VSA/VSM-404) is the baseband diversity technology that was originally developed through the commercial Research & Development (R&D) effort at Alcatel-Lucent over a last several years. The technology has the ability to aggregate the bandwidth from multiple spectral slices to one larger virtual channel to achieve higher throughput. Since all information is combined into one aggregated channel, it also helps to the satellite users and network management system to improve the operational flexibility, efficiency, and resilience of the satellite resources and provides protection capability to mitigate the interfaces effects in the event of interferences occur. VSA/VSM-404 technology operates over a single gigabit ethernet interface that manages both control traffic and data traffic sending and receiving from and to the satellite modem. VSA/VSM-404 technology can work with either LAN or VLANs technology, but with VLAN it would be required less equipments to operate, easy to manage the configuration and lowering the cost of captial equipment and operation cost to the user. A Cisco switch as depicted in the diagram below [figure 1] is a device that is used to send and forward the traffics between the users. Cisco switch works together with the VSA/VSM-404 to provide the additional routing, quality of service capability to ensure the network performance is achieved.
The management port and data port on the VSA/VSM-404 ethernet interface can either be configured in the same subnet or different subnet to support its integration into the architecture with satellite modem.
A little technical background on the technology itself to get reader familiars with the technology and teh baseband diversity integration project that will be discussed through the article. From the management perspective, we are trying to determine if it is necessary to physically separate the management IP from the data IP of using two separate switches which will cost us a lot of more, with increase manpower to maintenance the network and configuration or can we just simply support the baseband project technology integration with using one switch with VLAN concepts. Less equipments/technology required would cost less to procure them and usually reduce maintenance costs to maintain and operate the network which would results additional gain for the company.
For the purpose of this article management IP and control IP can be used interchangeably. The VSA/VSM-404 and the VSA can be used interchangeably.
Keywords: Logical, Network, VLANs, Management, IP, Data, Separation, Physical, LANs, Operate
Practical Scenarios-Looking at the Scenario Evaluation from the Technical Perspective and Management Perspective
Scenario # 1 Technical Perspective: The Data IP Address is on The Same Subnet as the Management IP Address of using VLANs.
To differentiate between the two channels on the VSA, let’s use Transmit Chanel 0 (Tx 0) and Transmit Channel 1 (Tx 1) in this example. VSA is used UDP port number and assigned VLANS to separate between the two channels together. For example, Tx 0 used VLANs 2 with UDP port # 1234/1234 and Tx 1 used VLANs 3 with UDP port # 1235/1235 so they can logically separated the traffic between the channels. This level of separation is done internally on the VSA. Because the management port is sharing the same network address as the data port, the broadcast traffic sent from one port would impact the data destined for the other port which shared the same network segment. Data collision would be expected as the result of two devices on the same network segment attempting to transmit data at exactly the same time. This practice is not recommended because the broadcast domain of the management IP address and the traffic IP address is resided within the same Local Area Network (LANs). This configuration will also lead to vulnerabilities in the network’s security and is not an efficient way to operate the network as it leaves the network to open attack.
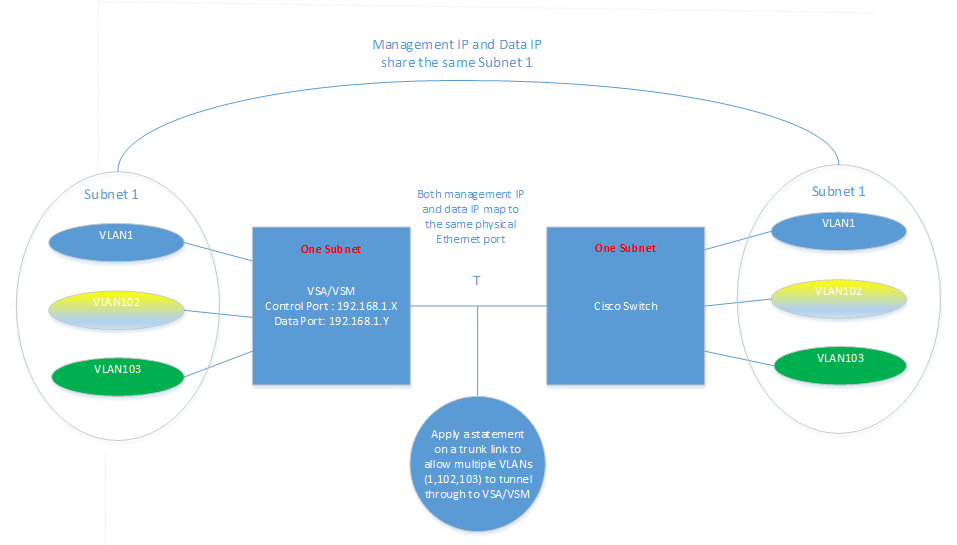
Figure 1: Data IP address and Management IP address on the same subnet (Ref to Subnet 1 in Figure 1 diagram).
In Figure 1, we have both Management IP and Data IP are mapping to the same physical Ethernet port. One broadcast domain is sharing between Data IP address and Management IP address. VLANS were used to connect to different modem blades. The left and the right network were sharing the same network
Scenario # 1 Management Perspective:
| A Feasible Approach but not recommended, why? | Reasons | Impact to Management |
| Data transmission collision | One network was being shared between data and control which incurs the possibility of data collision when the information is transmitted at the same time | Downtime, Network Outages, Loss of Revenues |
| Open Vulnerability | Intruder could gain access to a second port once it gets in the first port because both ports were shared the same network | Operational risks, loss of productivity, damage to equipments, loss of revenues, personal identification information may be compromised, costly to repair the network and clean it up |
Scenario # 2 Technical Perspective: Data IP Address is on Different Subnet From the Management IP Address of using VLANs.
This scenario provided an independent broadcast domain to each network. Each VLAN acted like a separate physical bridge. Here each broadcast domain resided within a different LAN segment unlike the previous scenario where the broadcast domains resided within the same LAN segment. Only broadcast frames that belong to a certain VLANs are forwarded to that particular segment. This will reduce the unnecessary traffic and collisions. Each segment has an independent and separate domain that isolates it hence you would not have the situation where data problems on one LAN propagate to the other LAN. Virtual LAN should be maintained as separated collision domain, so each segment of the VSA only contends with other hosts on the same segment for access. Therefore, the Scenario # 2 operation is much safer than the Scenario # 1 because the control IP and data IP are separated by different subnets. It is safe for certain levels of secure these information, all the traffic from multiple VLANs still flows over the same physical wires, while assuring the network traffic is isolated from each other. A host with access to that traffic (i.e. on the same subnet) can always be configured into the mode and view all of the traffic destined for that subnet on the wire.
Obviously, the use of logical VLANs reduces a lot of network vulnerabilities since the switches are controlling which data actually appears on which ports, however as the matter of fact that the VLANS share the same physical wire means that risk vulnerability still exists. Compromising the network security is often much easier than compromising physical or local security. If the IP address of the control port is compromised, the attacker can map to that IP address and access to the information on the control plane. It is possible for the IP address to be compromised, however, it’s not as easy as it sounds. Attackers must be able to get through multiple layers of security before they can even get to the information which would involve breaking the router authentication, the port security, and perhaps the access control list (ACL). Because the Management IP and Data IP are flowing to the same physical Ethernet port does not mean that they can not have a separation between them (i.e. virtual or effective physical separation). The separation is done virtually or logically at the data link layer (OSI Layer 2) to create a separation between different VLANs on both the switch and the VSA. The designer/engineer must ensure the IP assignments/configuration is done properly so that the traffic will not be routable between VLANs. In addition, port security features add additional layers of security in the Local Area Network (LAN) network. They are used to secure the IP switch port. The switch can be setup to lock down the ports based on MAC address to prevent unauthorized access to the VSA. Port security enhances the LAN security. This capability to separate the management IP from the data IP logically is exits today on the VSA. Thus making it unnecessary to have a physical separation between ports on the VSA.
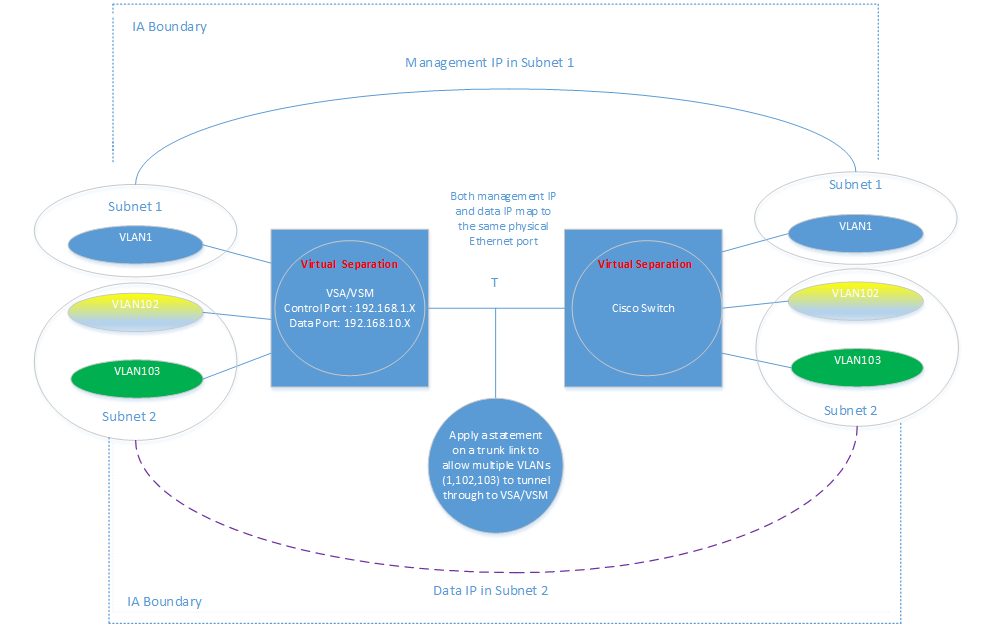
Figure 2: Data IP address and Management IP address on different subnets (ref to subnet 1 and subnet 2 in Figure 2 diagram).
In Figure 2, we have both Management IP and Data IP are mapping to the same physical Ethernet port.
Scenario # 2 Management Perspective:
| A Feasible Approach and recommended, why? | Reasons | Impact to Management |
| Separation of two subnets via VLAN Technology | To prevent data collision when the information is transmitted between the data plane and control plane because they both transmit and receive in separate subnets/networks that is separated by VLANS | No Downtime, No outage, Keep the company maximize profits and maintain their revenue |
| Multi layer of security through port security and locking down the unused ports | Enable Security protection to the users and the whole network operation | A little or No risk to daily operation, Increase productivity , keep customer happy and protect the customer personal information which is a big deal |
| Commercial off the shelf product available | Can be acquired quickly without waiting for a product to be developed, less risks | Positive gain to buy the product off the shelf, don’t have to spend extra money for the product to be developed |
Scenario # 3 Technical Perspective: Physical LAN Separation Between the Control Port and Data port on The VSA/VSM404 (does not exist today). From program management perspective, is this technical approach feasible and affordable to implement in a company network?
The answer to this question is yes it is feasible and it can be done properly with physical LAN technology separation implementation for management traffic and the data traffic, however, from the cost perspective it is not affordable because user will have to spend twice as much costs on the hardware versus one switch with VLAN solution.
If the IP address of the control port is compromised for whatever reasons, the attackers still need to know the correct port on the switch and they would need to be physically connected to it before they can access any information on the M&C control plane. The proposed approach used in the Scenario 2 is as safe and effective as Scenario # 3. Both of these approaches are cheaper and will impose fewer security risks to operate the VSA. Scenario# 2 is currently available to support this capability without requiring a modification to the hardware and/or software of the VSA. However, if the Scenario 3’s approach is chosen then it would require a modification to the hardware, and may be software, which would incur additional costs and time to implement it.
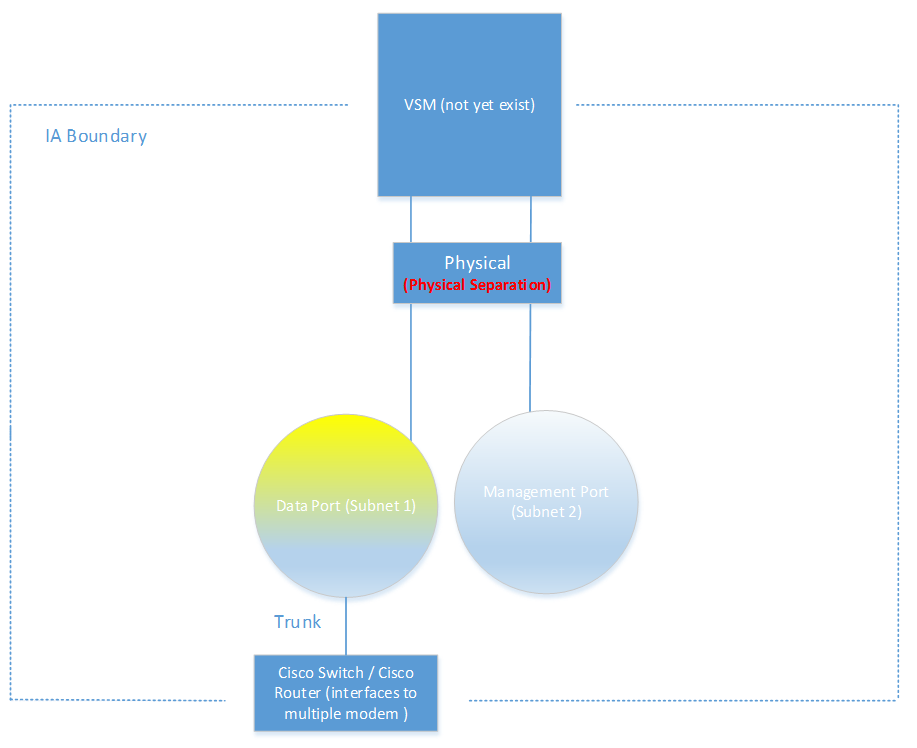
Figure 3: Data IP address and Management IP addresses are on different subnet (subnet 1 and subnet 2 in Figure 3 diagram).
In Figure 3, Both Management IP and Data IP will be mapping to the different physical Ethernet port). (Not yet exits).
Scenario # 3 Management Perspective:
| Feasible Approach and not recommended why? | Reasons | Impact to Management |
| Separation of two subnets via LAN | Main reason is cost, to have a physical separation, user will have to buy two switches in order to have LAN separation between the two networks instead of using one switch with VLAN technology concept | -Increase company’s capital cost (double a cost expenses)-Increase company maintenance cost to operate and manage the network-If the hardware is not available commercial off the shelf then user will have to spend extra money to the company to develop this capability before it can actually put into use |
| This solution is not currently available in the market | Time and money will spend to get this feature develop | Negatively impact to the network integration, risk depends on whether the feature can be developed on time and successfully |
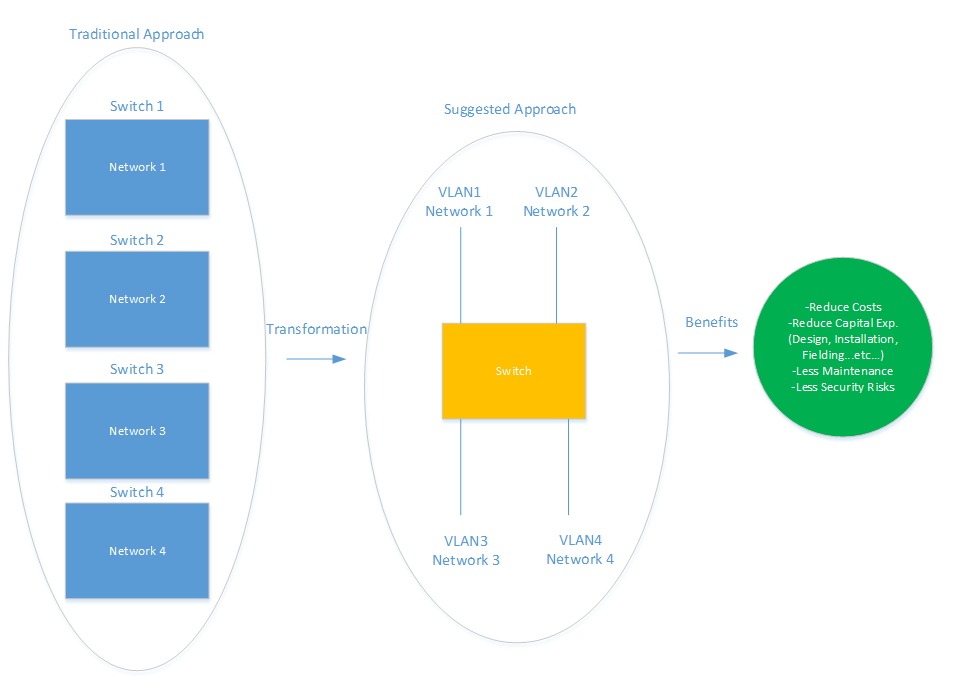
Figure 4. Traditional Approach vs. Suggested Approach for VLAN, looking at from the cost saving management perspective
Recommendations and why we choose VLAN over LAN technology? How would it contributed to decision making process?
Summary Benefits of using VLAN Technology from Program Management and Decision-Making Perspective:
- Cost reduction or cost saving from a need for upgrading to the expensive network and provided bandwidth efficiency for sharing with multiple users in the network. Captial expenses could be saved by employing the same switch throughout the building insteading of installing one switch per building
- Better control and management: Users are sharing the same vlan segment across the network so it make it easier to manage and control everyone from the same switch over multiple switches in different locations, in this case, less man power is needed for monitor and control the network
- Improve network performance and security: users can be placed in different vlans so one user can not see other user is doing on the network, that provides better security practices between network segments
- Simpler solution: Vlan concept technology is pretty easy to adopt to upgrade the network
In addition, there are other benefits of using the VLAN technology for small businesses. One of the benefits is reducing the capital costs because less hardware will be implemented with VLAN. Multiple bridge domains can be shared logically on a single switch platform. VLAN would work great for small businesses, especially for those businesses that will expand their network size for future growth. Having different switches to isolate traffic between different networks is not recommended because it is costly and more hardware will need to be maintained. More hardware will be required, more wires and more connections in order to connect the network together, this will pose more security risks if the network is not managed and protected carefully. VLANs can be used to great effect by small businesses to bolster security, increase usability, and improve network performance. We can use VLANs to separate different type of traffics between different users onto their own protected networks. VLANs through the wired method are referred to VLANs through the wired. VLANs can also support the wireless network. With a wireless VLAN, you have a separate, mini network that exists within your wireless LAN. A wireless VLAN has the added benefit of being able to segment wireless traffic into groups, keeping certain types of traffic separate from others. VLANs are great for increasing your business’s network security, which also makes your employees and clients feel safer and benefits your company’s reputation. All those advantages aside, there are still several other reasons why VLANs benefit a small business.
Bibliography:
Lammle, T. (1999). Cisco Certified Network Associate Study Guide 7e. Alamdeda, CA: Sybex, Inc.
Kotfila, D. Moorhouse, J. Wolfson, R. (2008). CCNP Implementing Secured Converged WANs (ISCW 642-825) lab portfolio. Indianapolis, IN: Cisco Press



