
On Strengthening Fraud Detection Instruments
This paper analyzed the effectiveness of currently selected fraud detection instruments; the Fraud Triangle, the Fraud Scale, Fraud Diamond, A-B-C analysis, the MICE model, and the Meta-model. The paper used secondary sources, including the 2020 Association of Certified Fraud Examiners’ Reports to the Nations on Occupational Fraud and Abuse, the 2018 report to the Nations Canadian edition, Research reviews, and other published works. It utilized content analysis by comparing the six fraud detection instruments. The outcome shows that the current fraud detection instruments did not go far enough to uproot and replace the fraud triangle. Moreover, these tools do not wholly eliminate occupational fraud. This work upheld the fraud triangle along with some precedent researchers and practitioners. However, it suggested “willingness” to reinforce the opportunity side of the fraud triangle. Future studies could search for efficient and effective fraud detection instruments not just to measure occupation fraud but also to monitor early behaviors and measure the mind of a fraudster.
Introduction
This article paper examines the effectiveness of current fraud detection instruments that consist of the Fraud Triangle, the Fraud Scale, the Fraud Diamond, the A-B-C analysis, the MICE model, and the Meta-model.
Stats show that a weak fraud detection instrument increases the opportunity for occupational fraud. For instance, theft by employees and other insiders cost companies an estimated 5% of their annual revenues—almost $4 trillion in global fraud loss. Moreover, the report revealed that 89% of assets misappropriation with a $114,000 median loss per incident, 38% of corruption with a $250,000 median loss per incident, and 10% of financial statement fraud with an $800,000 median loss per incident (A.C.F.E., 2018)
First, it created the fraud triangle to determine the reason behind a fraudster’s fraudulent behaviors. And other authors designed different tools to innovate and uproot the fraud triangle. Still, these instruments appear not essentially the most effective (Kummer et al., 2015).
This paper will not discuss all known fraud detection instruments but will examine the effectiveness of the five selected fraud detection tools.
Besides that, the paper also emphasizes mainly the opportunity. Opportunity is one of the three legs of the fraud triangle, likewise pressure and rationalization. Abrecht S. (2014) noted that none of these elements alone would be sufficient to result in embezzlement.
However, A.C.F.E considered the opportunity being the substance that could increase the rate of occupational fraud the most, and it is the one element a company can control.
Nevertheless, Huber (2017) noted that the fraud triangle had outlasted its helpfulness, the value it had never had since its beginning, and Okan Okten (2018) mentioned its failure to bring a paradigm change in the control field.
This study aims to determine whether the existing fraud detection instruments could effectively eliminate occupational fraud.
Objectives/Aim
To examine the effectiveness of fraud detection instruments:
– Comparing the content of the selected fraud detection instruments.
– Find an appropriate tool for fraud detection by comparing the five selected functionalities.
The paper compared the six selected fraud instruments using content analysis and evaluated the similarities and differences between these tools. Mainly compared the posterior model tools to the fraud triangle. This approach seems adequate to find the answer to the effectiveness of fraud detection instruments currently business organizations are using.
The paper used secondary sources, including the 2020 A.C.F.E report to the Nations on Occupational Fraud and Abuse, the 2018 report to the Nations Canadian edition, Research reviews, and other published works. This paper is an extract from Christopher Umba’s Ph.D. dissertation (Umba, 2021).
The outcome of this work is predictive, and it does not create a new theory but advances the study.
Result
This paper analyzed the effectiveness of selected fraud detection instruments, including the fraud triangle, fraud scale, fraud diamond, meta-model, A-B-C analysis, and mice model.
The collected data revealed that current fraud detection instruments do not eliminate occupational fraud. However, many businesses still uphold the fraud triangle, even though many scholars have raised some critical weaknesses of this tool.
The paper used data from a secondary source to advance this work: A.C.F.E. 2018 report to the Nations Canadian edition, Canadian association banks, Statisca, research reviews, and other published works.
The data collected was relevant to understanding the importance of using an effective fraud detection instrument searched in this paper. However, more data is needed to further the research.
This section addressed: data presentation, description, analysis, and findings.
Data presentation
At first, a short description of each tool is in the appendix, but figure 1 regroups all the selected and compared fraud detection instruments.
| Figure 1 | |||||||
| Fraud Detection Instruments | |||||||
| Name | Description | ||||||
| Fraud Triangle | Pressure | Opportunity | Rationalization | FT= 3 elements | |||
| (Cressey, D.,1973) | |||||||
| Fraud Scale(Albrecht et al.,1984) | Pressure | Opportunity | Personal Integrity | FS= 2 elements | |||
| Of the F.T. + 1 | |||||||
| New element | |||||||
| Fraud Diamond(Wolfe & Hermanson, 2004) | Pressure | Opportunity | Rationalization | Capacity | FD= 3 sides of F.T. | ||
| + 1 new element | |||||||
| Meta-model | Pressure | Opportunity | Rationalization | Personal Characteristics (at all hierarchy levels) | M.T. =3 sides of | ||
| Dorminey et al. (2012) | FT+1 new element | ||||||
| A-B-C Analysis (Ramamoorti et al., 2009) | A-Bad Apple (Individual fraud) | ABC= 1 element | |||||
| B-Bad Bushel (Collusive fraud) | Same as pressure | ||||||
| C- Bad Crop (Culture and social fraud) | But noted that the | ||||||
| Behavior is the root | |||||||
| Cause of fraud | |||||||
| Mice Model | M- Money | MM= 3 FT(Money, | |||||
| Kranacher et al. (2011) | I-Ideology | Coercion= pressure | |||||
| C-Coercion | & Ego= | ||||||
| E- Ego | rationalization) +1 | ||||||
The data displays the six different fraud detection instruments side by side. On the one hand, the first four include the fraud triangle (F.T.), fraud scale (F.S.), fraud diamond (F.D.), and meta-model (M.T.). These models contained most of the fraud triangle elements except in the fraud scale, and rationalization is replaced by personal integrity. The fraud diamond adds the capacity to commit fraud, and the Meta-model adds personal characteristics.
On the other hand, the last two fraud detection instruments present differently the elements perceived to lead someone to commit fraud, which could help investigate fraud. They seem to be part of perceived pressure. The A-B-C Analysis emphasizes personal, group, and community fraudulent behaviors, while Mice Model (MM) stresses the elements of pressure to commit fraud.
As one can see, most of the selected fraud detection instruments are built on the fraud triangle, and the attempt did not go far enough to change it completely. The appendix provides a detailed description of each fraud detection tool.
Findings
After the content analysis of each fraud instrument tool element compared to the fraud triangle, besides the fraud triangle, the current tools fraud scale, fraud diamond, meta-model, A-B-C analysis, and mice model did not go far enough to uproot or replace the fraud triangle. Moreover, they do not wholly eliminate occupational fraud. In the absence of a perfect tool, this work upheld the fraud triangle as it is considered by some precedent researchers and practitioners, for instance, the association of certified fraud examiners (2018). Therefore, the opportunity, which is one of the legs of the fraud triangle, should be reinforced.
Discussion
The findings suggest the lack of a perfect fraud tool, and the current fraud detection instruments appear to not wholly eliminate occupational fraud, which is consistent with precedent studies. Kummer et al. (2015) argued about the ineffectiveness of the tools, and Okten (2018) noted the absence of a paradigm change.
This section mainly discusses the strengths and weaknesses of the selected tools (the fraud scale, fraud diamond, meta-model, A-B-C analysis, and mice model) compared to the fraud triangle and should also address the “opportunity” leg of the fraud triangle. Besides the enormous contribution to the current fraud detection tools, this work suggests a willingness to reinforce the opportunity of the fraud triangle.
Fraud Scale, from its conception, the fraud scale tool displayed in figure 3, was supposed to be an alternative to the Fraud Triangle. Albrecht et al. suggest that higher pressure, greater opportunity, and low personal integrity increase the likelihood of occupational fraud within an organization. However, personal integrity seems complex to measure and unpredictable before a fraudster commits fraud—for instance, in the Madoff scandal.
Even when Albrecht et al. replaced rationalization with personal integrity or a code of ethical behavior that each person adopts, rationalization is still a deeply personal process that varies from one individual to the next. In addition, it is based on the subjective judgment to commit fraud.
An investigator can observe personal integrity through a person’s past behavior and decisions. He could also use an employee’s commitment to ethical conduct and his tendency to fraud for assessment. Personal integrity seems consistent with Cressey’s description of rationalization. Albrecht et al. did not change anything to the fraud triangle. Why did they not address the opportunity, the one side of the fraud triangle that appears to open the door to occupational fraud?
However, stats show that when a company establishes robust internal control, it minimizes the (Opportunity) occurrence of fraud.
Fraud Diamond, Wolfe & Hermanson (2004) added a fourth side, “capability,” to the fraud triangle by naming it a fraud diamond. They assumed that it requires a person with the capability to recognize an unsecured doorway to fraud and work to commit fraud. They also considered capacity as an observable trait for fraud, mainly when considerable sums of money are involved or the fraud lasts a long time. For example, the person is persuasive and can coerce others to commit or conceal a fraud.
In the same way, Mackevicius & Giriunas (2013) argue that not every person who possesses pressure, Opportunity, and Rationalization might commit fraud but can proceed to fraud with the capability.
However, Gbegi & Adebisi (2013) assert that although the fraud diamond adds up the fourth variable, “capability,” to the fraud triangle and expecting filling the gap in other theories, the model alone is an inadequate investigation tool. The two sides of the fraud diamond (pressure and rationalization) are unobservable, ignoring critical factors like the national value system. Still, the Diamond fraud model does not provide a reading of a fraudster’s mind that could offer a preventive tool.
A-B-C Analysis, besides the capability to recognize an unsecured doorway to fraud, Ramamoorti et al. (2009) state that behavior is the root cause of fraud, and someone can identify it by observing an individual (Bad Apple), a group (Bad Bushel), or a community’s actions (Bad Crop). They emphasize that the most dangerous is a Bad crop in the A-B-C stage of the fraud analysis model. A Bad Crop characterizes leaders’ moral deficiency in an organization, quickly spreading to their subordinates. Since it spreads throughout the organization, fraud eventually becomes a culture in the congregation, from the leaders to the assistants.
Dorminey (2012) called a bad crop an epidemic because it affects a large population and pollutes most of society. However, employees should tap into self-value (conscience) to change things.
A company should establish a mechanism to prevent fraud at the workplace; for instance, robust internal control can minimize the opportunity for fraud. Additionally, the creation of a tool capable of reading a fraudster’s early behavior is required. However, as one can see, the reading of fraudulent behavior comes after the fraud occurred. Despite the existing tools, the exact machine for reading the mind of a fraudster is not yet there.
Money, Ideology, Coercion, and Ego (M.I.C.E) go beyond financial pressures and provide an increased set of motivations beyond a non-shareable financial pressure that could drive fraud. Dorminey et al. (2012) note that money and ego are common motivations in fraudulent behaviors; Ideology is uncommonly different from coercion. Moreover, ideology seems probably a less common incentive for white-collar crime. Allan (2003) identifies egotists as the most common personality type among fraudsters. For example, the case histories of Madoff, Stanford, Enron, and WorldCom.
The M.I.C.E seems to carry out the same fraud component as in the fraud triangle pressure, opportunity, and justification to commit fraud. However, the fraud triangle and the M.I.C.E approach do not explain every fraud act and all fraudulent incentives. Moreover, some of the fraud elements fall into more than one category.
The M.I.C.E model provides professionals with a general conception to consider the possibility of fraud.
Meta-model emphasizes the essential role of anti-fraud efforts between the fraudster (the Fraud Diamond) and the criminal act (the Triangle of Fraud Action) (Dominey et al., 2012). These anti-fraud interventions, such as internal controls and anti-fraud measures, are found outside the perpetrator’s control.
A.C.F.E (2018) states that anti-fraud controls were correlated with lower fraud losses and quicker detection. For instance, the A.C.F.E report compares organizations with specific anti-fraud controls against organizations lacking those controls and found that where controls were present, fraud losses were 12 percent to 56 percent lower, and frauds were detected 33 percent to 58 percent more quickly.
Still, they are likely to influence the would-be fraudster’s judgment of the probability of success in fraudulent conduct, concealment, and conversion. Therefore, researchers, business leaders, and governments should focus the most on the opportunity to commit fraud.
Fraud triangle: the analysis shows that the fraud triangle out-stands the precedent-examined fraud detection tools. The fraud triangle communicates the conditions under which fraud may occur and constitutes an essential contribution to fraud theory. The Fraud scale, Fraud diamond, the Mice model, the A-B-C model, and the Meta-model approaches analyzed have reinforced the idea and add up new tools to the fraud theory. Some of these fraud tools are still not implemented or used, but the fraud triangle continues to be modified.
Nevertheless, Huber (2017) discusses that the fraud triangle is obsolete and initially had no value. So, it is useless and should be discarded in forensic accounting research and other financial crimes. On the contrary, he proposed to consider the n-dimensions of financial crime that should be present in any model that attempts to explain, predict, prevent, detect, and prosecute financial crimes, of which fraud is only a subset.
Tools can be practical, but a perpetrator’s moral state plays a crucial role in occupational fraud. So, a user of the tool or investigative device is essential to an effective result.
Barrett (2013) argues about the inclination that something is not precisely correct when the number does not thoroughly add up or observe the red flags. Singleton et al. (2006) discuss that red flags are critical and helpful in designing effective detection methods and processes (p.168).
The Fraud Triangle, and its elements, are not accurate prognosticators of fraud but rather are elements to explain and understand a fraudulent actor after the fact. Therefore, facts and evidence should be the foundation of any case. (Marks, J. T. C., 2020).
However, studies suggest the need for a permanent update and change to close the opportunity loophole. A.C.F.E. (2018) states that the perceived opportunity can arise from several sources, including poor internal controls, poor training, poor supervision, lack of prosecution of perpetrators, Ineffective anti-fraud programs, policies, and procedures, and Weak ethical culture (e.g., poor tone at the top). So, a person must see a way to commit fraud with a lower risk of being caught.
Contrary to Cressey’s theory of the three necessary factors for fraud, that includes pressure, Opportunity, and Rationalization. Schuchter (2015) argues that only opportunity seems a universal precondition of acts defined by others as a fraud because the pressure and rationalization are silent in most schemes unless there is a move to commit fraud.
As one can see, the opportunity is taking more resources and attention. Still, the opportunity is an outside element of a fraudster and a magnet for fraud. The implementation of robust internal control can reduce the opportunity to commit fraud. The other two sides of the fraud triangle, pressure, and rationalization, are unseen fraudsters’ internal elements that require more resources to produce adequate tools. The fraud triangle is a triangle, so all three elements should be present for fraud to occur.
Although the fraud triangle is the most widely accepted model for why people commit fraud, A.C.F.E. (2018) acknowledged the fraud triangle’s capacity and limitations. Moreover, it is necessary to recognize that other studies have suggested different tools besides the fraud triangle. Some tools attempted to update the fraud triangle, and others completely replaced it. Still, the fraud triangle survived and continues to be updated and utilized.
The paper reaffirms that the opportunity is still a loophole when an informed fraudster can observe and willingly commit fraud because someone can perceive pressure and rationalization of fraud, but in the absence of the opportunity, fraud will not occur.
Cressey called the second leg of the fraud triangle perceived opportunity, which characterizes the strategy by which a fraudster can commit fraud. The individual must see how he can misuse his trust situation to take care of his money-related issue with a low danger of getting captured. Once the perceived opportunity is present, it gives way to pressure and rationalization in fraudulent behaviors.
Wolfe and Hermanson (2004) argue that it is not just the perceived opportunity that should action the fraud, but a person’s capability to commit fraud is necessary or must be present. Capability requires the position and information at the time someone commits occupation fraud. However, Albrecht et al. argue that low pressure and lesser opportunity but high personal integrity decrease the chances of fraud. Still, a fraudster can commit fraud even in lesser opportunities with a willingness (Umba, C., 2021)
Money, Ideology, and Coerce are external conditions that fall in the pressure category, and ego inside elements like rationalization in the fraud triangle. Still, it requires a willingness to proceed with fraudulent behavior, to paraphrase Ramamoorti et al., who argue that fraud results from behavior in the A.B.C. model.
This work found that willingness is key to a fraudster’s decision to commit fraud.
Figure 6
Fraud Diamond Model with a moving star
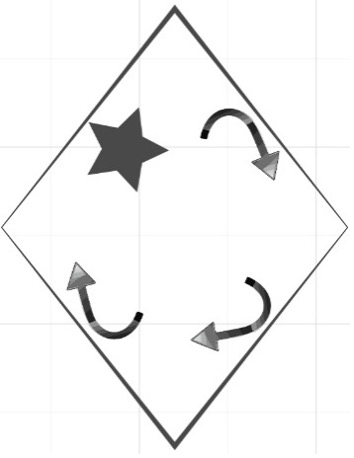
Umba, C. (2022)
Description:
- Star represents a willingness to commit fraud because even when there is pressure, opportunity, rationalization, and capability, a fraudster’s willingness is a key to committing occupational fraud. The star moves whenever one side of the diamond shape is in action.
- The four shapes of diamond are equal to the fraud diamond (Wolfe and Hermanson, 2004)
This work suggests willingness because it is a catalyst of fraud than a capacity to fulfill something wrong or right. When presented with complex emotions, willingness is a person’s stance (Moran, 2012). Willingness here becomes a state of being willing, the readiness of the mind to do or abstain. That is the inside personal resolution or an intention to fulfill something or commit fraud. One might do something, but one still needs the inside resolution to go ahead with the plan. It is not the same as Cressey suggested about the motivation that lines up with a rationalization.
Motivation is a reason to accomplish the perceived pressure. Motivation can be external (extrinsic) and internal (intrinsic), but willingness is only an internal force. Willingness is a personal choice to do something, even in the absence of outside pressure. As one can see, someone, by self-choice, can resolve to fulfill the wrong decision, even knowing the consequences. For example, Bernie Madoff, an American former market maker, investment advisor, and financier, knew the Ponzi scheme’s implications. However, he resolved to continue with a massive undertaking that brought him to a longer prison sentence.
The opportunity for fraud may be a sign of weak internal control within a business organization because auditors are there to deter fraudulent behaviors; this is one of the audit missions. Sometimes it is rare to see or measure the level of an opportunity or the chance that a fraudster must commit fraud until one discovers fraud within a company. Business management should close a loophole or remove the magnet from occupational fraud.
Laycock (2012) asserts that opportunity causes crime, but crime science could affect crime control in at least four ways: First, it can help comprehend the crime’s nature. Secondly, it can help avoid wrongdoings from happening in the first place; thirdly, it can assist the detection of offending through the forensic sciences; and finally, it can provide methods that help test hypotheses about the opportunities.
Future studies can focus on an intelligent tool capable of anticipating the unknown before a fraudster’s actions because all the current tools focus on known occupational fraud with its consequences on the business entities.
This paper examined the data collected from the A.C.F.E. 2018 report to the nation, the Canadian version, Canadian association banks, Statisca, Research reviews, and other published works. Noting the frequency and magnitude of the increase in fraud, it affirmed that weak fraud detection instruments enhanced the opportunity for occupational fraud.
Other authors have suggested different tools and sick to replace the fraud triangle. This work indicated that adding willingness to opportunity should contribute as a deterrent to the increase of occupational fraud. It is also a fact that opportunity is still one tool a company can use to manage more than perceived pressure and rationalization that are unshared internals’ fraudsters.
Further studies could search for adequate practical measurements to monitor and measure not just occupational fraud but readingthe mind of a fraudster anticipatively. Because to change something, someone should know it and measure it.
References
Adebisi, J. F. (2013). The New Fraud Diamond Model-How Can It Help Forensic Accountants In Fraud Investigation In Nigeria? Gbegi, Do. European Journal of Accounting Auditing and Fiancé Research, 1(4), 129-138.
Albrecht, W. S. (2014). Iconic Fraud Triangle endures. Fraud Magazine. https://www.fraud-magazine.com/article.aspx?id=4294983342
Allan, R. (2003). The human face of fraud. C.A. Magazine. http://www.camagazine.com/archives/printedition/2003/may/regulars/camagazine23440.aspx
Association of Certified Fraud Examiners. (2018). Report to The Nations Canadian Edition. Acfe.Com. https://www.acfe.com/uploadedFiles/ACFE_Website/Content/rttn/2018/RTTN-Canada-Edition.pdf.
Barrett, B. (2013, August 19). Inside the Mind of the White-Collar Criminal. AccountingWeb.Com. https://www.accountingweb.com/technology/trends/inside-the-mind-of-the-white-collar-criminal
Canadian Bankers Association. (2020). Learn more about how banks in Canada are protecting Canadians from fraud. Cba.Ca. https://cba.ca/protecting-canadians-from-fraud.
Cressey, D. R. (2003). Other People’s Money: A Study In The Social Psychology Of Embezzlement (4th ed.). Wadsworth Publishing Company.
Dorminey, J., Fleming, A. S., Kranacher, M. J., & Riley, R. A. (2012). The Evolution of Fraud Theory. Issues in Accounting Education, 27(2), 555–579. https://doi.org/10.2308/iace-50131
Huber, W. (2017). Forensic accounting, fraud theory, and the end of the fraud triangle. Forensic Accounting, Fraud Theory, and the End of the Fraud Triangle, 12 (2).
Kummer, T. F., Singh, K., & Best, P. (2015). The effectiveness of fraud detection instruments in not-for-profit organizations. Managerial Auditing Journal, 30(4/5), 435–455. https://doi.org/10.1108/maj-08-2014-1083
Laycock, G. (2012). Editorial introduction to opportunity makes the thief. Really? And so what?” Crime Science, 1(1). https://doi.org/10.1186/2193-7680-1-2
Mackevicius, J., & Giriunas, L. (2013). Transformational research of the fraud triangle: Vol. 92(4), 150–163. Ekonomika.
Marks, J. C. T. (2020, January 17). (Advanced) Meta-model of Fraud – Two triangles combine for better fraud case comprehension. BoardAndFraud. https://boardandfraud.com/2018/06/27/meta-model-of-fraud-two-triangles-combine-for-better-fraud-case-comprehension/
Moran, D. J. (2012, January 12). When More Isn’t Enough: Willingness to Change. Psychology Today.https://www.psychologytoday.com/ca/blog/when-more-isnt-enough/201201/willingness-change
NACD Board Fellow, & Marks, T. (2018). (ADVANCED) META-MODEL OF FRAUD – TWO TRIANGLES COMBINE FOR BETTER FRAUD CASE COMPREHENSION. https://boardandfraud.com/2018/06/27/meta-model-of-fraud-two-triangles-combine-for-better-fraud-case-comprehension/
Okan Okten, P. (2018). Paradigm shifts in causes of fraudulent actions: Triangle, diamond, and the others. Journal of Business Research-Turk, 10(3), 655–669.
Ramamoorti, S., Morrison, D., & Koletar, J. W. (2009). Bringing Freud to Fraud: Understanding the State-of-Mind of the C-Level Suite/White Collar Offender through “A-B-C” Analysis. eCommons, 71. https://ecommons.udayton.edu/acc_fac_pub/71/
Schuchter, A., & Levi, M. (2015). Beyond the fraud triangle: Swiss and Austrian elite fraudsters. Accounting Forum, 39 (3), 176–187. https://www.tandfonline.com/doi/full/10.1016/j.accfor.2014.12.001
Singleton, T. W., Singleton, A. J., Bologna, J. G., & Lindquist, R. J. (2006). Fraud Auditing and Forensic Accounting (3rd ed.). Wiley.
Umba, C. (2021). Fraudulent Accounting/Financial Behaviors: Impact on Small & Medium Canadian Business Organizations. (Unpublished doctoral dissertation). L.I.G.S. University.
Wolfe, D. T., & Hermanson, D. R. (2004). The fraud diamond: Considering the four elements of fraud.
Appendix
The Fraud Triangle
At first, this fraud model was referred to as the embezzlement process by Donald Cressey. He developed this model based on extensive interviews with convicted fiduciary duty violators. It was modified multiple times and later called the “fraud triangle” with three sides or legs: perceived pressure/incentive, opportunity, and rationalization/justification. The Fraud Triangle describes conditions in which fraud occurs.
Figure 2
The fraud triangle
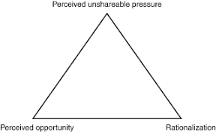
Cressey, D. (2003). Other People’s Money.
- Perceived pressure refers to a fraudster’s mindset at the personal and business level—for example, a need to meet earnings to sustain investor confidence.
- The opportunity defines the crime’s modus operandi and represents a business control system loophole that allows fraud to occur—for example, the presence of weak internal control in a business company.
- Rationalization refers to an individual’s justification for committing fraud. For instance, someone can say that they were only borrowing money.
The fraud triangle is vital to understanding an individual’s behaviors that lead to a decision to commit occupational fraud. Based on the three elements Cressey noted that embezzlement occurs simultaneously.
The Fraud Scale
Albrecht et al. (1984) developed the “Fraud Scale” model as an alternative to the Fraud Triangle after examining 212 fraud cases. The Fraud scale maintained the two elements of the Fraud Triangle’s features, “pressure and opportunity,” and dropped rationalization and replaced it with personal integrity, defining it as “the personal code of ethical behavior each person adopts.”
Figure 3
Fraud Scale
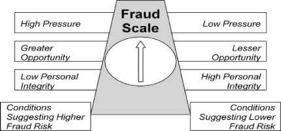
Albrecht et al., (1984). Deterring Fraud.
The data presents two conditions of fraud risk. One side suggests higher fraud risk caused by the presence of high pressure and greater opportunity but low personal integrity. Conversely, lower fraud risk is caused by low pressure and lesser opportunity but high personal integrity.
This tool operates as a dashboard that helps observe the conditions for fraud. The key to monitoring is personal integrity when low in the presence of high pressure and greater opportunity.
Fraud Diamond
Wolfe and Hermanson (2004) created the Fraud diamond to improve the Fraud triangle’s effectiveness by considering a fourth element, called “capability.”
They noted that apart from the incentive, perceived Opportunity, and Rationalization, an individual should have the appropriate abilities, coercion, skills, and personal traits to commit fraud. Thus, a fraudster will not overcome undetected controls without capability (figure 4).
Figure 4
Fraud Diamond
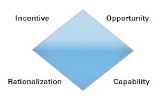
Wolfe and Hermanson (2004). The Fraud Diamond.
A-B-C Analysis
Ramamoorti et al. (2009) proposed the A-B-C model, or the “bad apple, bad bushel, and bad crop,” as part of the emerging discipline of behavioral forensics. The A-B-C analysis approach suggests progressing from an individual to a colluding group to a whole culture or environmental element (analyze and categorize fraud).
- The Bad Apple: Individual Personality Characteristics of those that Commit Fraud
- The Bad Bushel: Group Dynamics of Collusive Behavior
- The Bad Crop: The Larger Cultural/Societal Factors that Enhance or Permit Fraud
The A-B-C model contributed to fraud detection models with a new element pointing out that the root cause of fraud is behavior.
MICE Model
Kranacher et al. (2011) built upon the Fraud Triangle; another model named the “MICE model” Money, Ideology, Coercion, and Ego.
- Money: consists of all real or perceived financial pressures.
- Ideology: When ideology motivates fraud, the perpetrator often believes that their actions benefit the greater good or that following a particular rule is against their beliefs.
- Coercion: it describes the condition in which someone is unwilling but pressured to commit fraud.
- Ego: is closely related to the concept of financial pressure and involves the feeling of entitlement or pride.
This theory seems to expand the “pressure” leg of the fraud triangle. The M.I.C.E concept claims that financial gain does not explain the motivation of all fraudsters.
MICE model was created to modify the Fraud Triangle assessment providing more elements behind unsharable financial incentives and creating a possibility of collusion.
Meta Model
The Meta-Model framework provides an evolution of fraud analysis. It combines the fraud diamond that includes the traditional Fraud Triangle with the Triangle of Fraud Action in what has become known as the “meta-model of fraud.” It comprises anti-fraud efforts (Dorminey et al., 2012).
Apart from a firm’s preventive and detective procedures, the meta-model framework includes the personnel characteristics at all hierarchy levels; ethics, integrity, and ego; the anti-fraud control environment; tone at the top, hotlines; and fraud triangle criteria.
Figure 5
Meta-Model of fraud
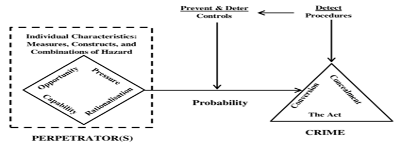
Dorminey et al. (2012). The evolution of fraud theory.
Data displays on the right side the specific fraud steps in the triangle of fraud crime—the financial crime, including the act, the concealment, and the conversion of benefits. In the middle of the meta-model of the fraud analysis between the perpetrator (the Fraud Diamond) and the criminal act (the Triangle of Fraud Action) are anti-fraud interventions such as audits or internal control to prevent, detect, and discourage the incidence and impact of fraud.
On the left side of the Meta-model of the fraud analysis, the Diamond triangle exhibits Cressey’s fraud triangle elements: Opportunity, pressure, and Rationalization. Furthermore, the capability to commit fraud.
As a result, the left-hand arrow is more considerable, indicating a higher likelihood of fraud before anti-fraud initiatives. Contrary, the right-hand arrow is thinner, indicating that the probability of fraud has decreased due to anti-fraud initiatives.
Author: Christopher Umba, student LIGS University
Approved by: Dr. Minh Nguyen, lecturer LIGS University



