The Techniques, Technology, Applications, and Software for Decrypting TLS and SSL Encrypted Data
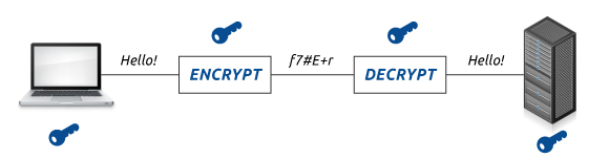
Transport Layer Security also referred to Secure Sockets Layer is considered as one of the well known public key cryptography application across the globe. The app is well known for securing the web browser. We will explore by understanding more on TLS/SSL, moving to their technique and technology. And finally, review applications and Software for decrypting TLS and SSL Encrypted Data.
TLS or SSL could be utilized in offering strong authentication in the communication session for both individuals, strong encryption of the data within the transit in between them as well as verification of data integrity within the transit. It is utilized in securing a wide range of critical business responsibilities like web browsing, e-mail-to-the server communication, database access, server-to-server communication, virtual private networking, software updating and so forth.
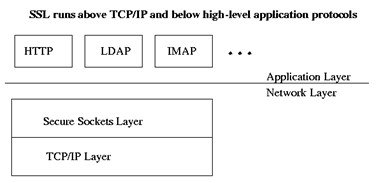
Understand https://security.stackexchange.com/questions/20803/how-does-ssl-tls-work, whenever improperly utilized, the TLS could offer the illusion of the security where communication is compromised. Furthermore, it is crucial to keep the certificates updated and checking thoroughly for the error conditions. In numerous situations, though not entire apps of the TLS, the integrity of communication is usually enhanced through the use of certificates issued by an external trusted certificate body.
Techniques
From, http://www.ipcopper.com/ssl_decryption.htm, the most significant components of the online business entails the creation of a trusted environment where probable clients feel confident while making the purchases. The TLS certificates create the basis for trust by enhancing secure connections, and the browsers offer visual cues like a green bar or lock icon in assisting visitors to understand the moment the connection is very secure.
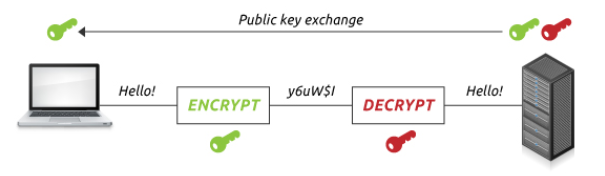
The SSL certificates possess key pair; that is, private and public key. Such keys are said to work all together in establishing an encrypted connection. Also, the SSL certificates comprise of the subject that is considered as the identity of the website or certificate owner. The SSL utilizes the two keys where the private key could sign and decrypt while public key could just encrypt.
Generally, the process is as follows:
- The SSL certificate is usually electronically signed by the Certificate Authority where the CA is then embedded within the browsers.
- Whenever the browser has initiated the SSL connection to the server, it tends to with the signed certificate. The browser authenticates the sign with correct CA certificates which are usually embedded in the browser. In case the authentication passes the extracts, the public key is used.
- Later the browser sends small information usually 50 to 60 bytes to the server. Such parcels are not necessarily recorded anywhere, and they are encrypted with a public key and could just be decrypted with corresponding or appropriate private key.
- Parcel forms the basis for the slightly bigger or huge key, utilized in encrypting the actual transmission of the content in between the server and browser. Such is usually faster cipher compared to that utilized by original parcel. There exist differences in how ciphers work, though general principles are similar.
While the packet captures the appliance of the original parcel of the information, it could display the encrypted state of the randomly selected short key. With no private key, one could not decrypt the information and view unencrypted content. Nonetheless, a computer taking part in transmission retains this key in the memory such that it could continue communicating with the server all through the SSL.
Basically, there are two approaches for decrypting the SSL transmissions. One means is usually hacking it, utilizing the brute force in exposing some irregularities which would assist with the decryption. One of the most straightforward means is utilizing private key.
On the other hand, users could opt to deploy custom packet capture solutions which have a tendency of employing a technique for storing and decrypting the SSL transmission. Customizing the IP copper packet with some features in enabling the SSL decryption, nonetheless, in numerous scenarios, it is not necessarily crucial in understanding the SSL matter. Generally, decrypting the SSL matter could have various ramifications as well as some unintended concerns.
Technology
From, https://www.digicert.com/ssl-cryptography.htm, technology in SSL encryption is explained. This covers symmetric and asymmetric keys as well as how they operate altogether in creating the SSL-encrypted connection. Further, it covers a diverse form of the algorithms which are utilized in creating the keys comprising of the mathematical equations which make them somehow virtually impossible in cracking.
Asymmetric Encryption
The asymmetric encryption utilized a separate or different key for decryption and encryption. Anybody could utilize encryption keys in encrypting the message. Nonetheless, the decryption keys are usually set as secret. This means only intended or anticipated receivers could decrypt messages. Some of the most common or popular asymmetric encryption algorithms entail the RSA; nonetheless, in this case, algorithms will be discussed later.
The asymmetric keys entail the 1024 or the 2048 bits. Nonetheless, keys lesser than the 2048 bits are usually no longer safer for use. The 2048 bits keys are said to have sufficient unique encryption codes where numbers would not be written here. Although bigger keys could be created, increased calculations problem is relatively significant that the keys more significant than the 2048 bits are hardly utilized. In putting it into perspective, this would take the average computer over 14 billion years in cracking the 2048 bit keys.
Symmetric Encryption
The symmetric encryption utilizes single key in both decrypting and encrypting the data. Both receivers and senders require a similar key for communication.
The symmetric key sizes usually range from 128 to 256 bits, hence, the bigger the size of the key, the harder it becomes to crack the key. For instance, the 128 bit has 282,340, 366, 938, 920,463, 374, 431, 607, 211, 768as well as 456 encryption code options. Hence, as one could imagine, the brute force usually would take longer in breaking the 128-bit.
Whether the 256 or the 128 bit is utilized relies on encryption abilities of both user and server software. The SSL certificates fail to dictate what size of the key to be utilized.
After reviewing from, https://hpbn.co/transport-layer-security-tls/, we can have a comparison which is stronger.
As the asymmetric keys are usually bigger compared to the symmetric keys, which data is mostly encrypted asymmetrically is usually tougher in cracking compared to data which is mostly symmetrically encrypted. Nonetheless, such does not imply that the asymmetric keys could be better off but instead of comparing their size, the keys ought to be compared by the ease of distribution and computational burden.
The symmetric keys, on the other hand, are smaller than the asymmetric one; hence, they need lesser computational burden than the symmetric ones. Nonetheless, symmetric have main drawbacks mainly if one utilizes them for securing the data transfer. Since the similar key is utilized for the symmetric decryption and encryption, both the server and recipient require these keys. In case, one could walk over and tell their recipient the keys; such would not be a big deal. Nonetheless, in case one is forced to send keys to the user halfway across the globe, one requires to concentrate on data security.
The asymmetric encryption has no such issues. So long one maintains their private key as a secret, nobody could decrypt his or her messages. One could distribute corresponding public keys with no worry about who could access it. Anybody with public key could encrypt the data through only an individual with private key could be in a position to decrypt it.
How the SSL Utilizes both Symmetric and the Asymmetric Encryption
The Public Key Infrastructure (PKI) usually entails a set of software, hardware, procedures, people as well as policies required in creating, managing, storing, revoking, distributing as well as utilizing the digital certificates. Also, the PKI comprise what binds the keys with the user's identities through the means or ways of CA. additionally, the PKI utilizes the hybrid cryptosystem and tends to benefits from utilization of both forms of the encryption. For instance, in the SSL communications, server’s SSL certificate comprises of the asymmetric private and public key pair. Session key which browsers and servers create within SSL handshake is usually symmetric as explained in the figure below.
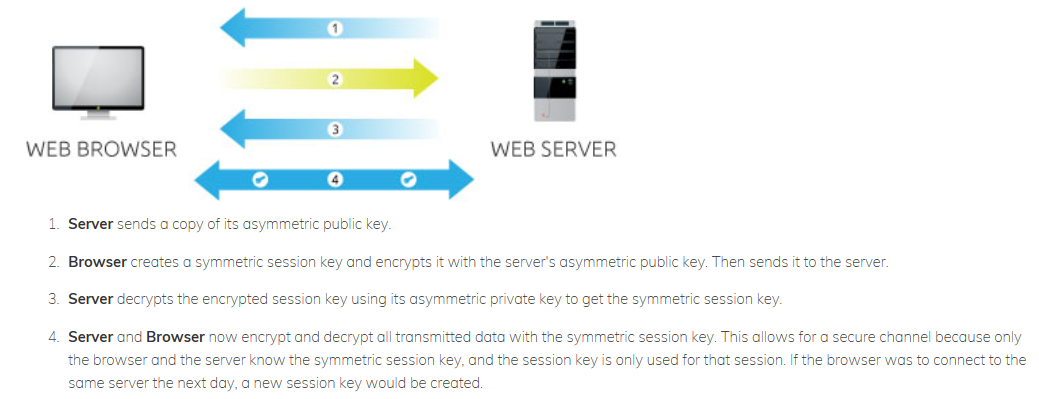
The Public-Key Encryption Algorithm
The Public-key cryptography utilizes the encryption algorithms such as the Elliptic Curve Cryptography and the RSA in creating the private and public keys. Such algorithms are usually based on the intractability of specific scientific issues.
With the asymmetric encryption, it becomes computationally easier in generating the private and public keys, encrypting the messages with public keys as well as decrypting the messages with private keys. Nonetheless, it is quite hectic for anybody deriving private keys on the basis of the public key only.
RSA
The RSA is usually based on presumed problems of factoring the more significant or large integers. The full decryption of the RSA ciphertext is believed to be an infeasible component on the assumption that there are no useful algorithms for the integer factorization.
The user of the RSA tends to create and publish products of the two more significant prime numbers alongside with the auxiliary values as the public key. The prime aspects should be maintained as secret. Anybody could utilize public key in encrypting the message, though only somebody with an understanding of prime aspects could feasibly decode these messages.
The RSA represents Ron Ron Rivest, Adi Shamir as well as the Leonard Adleman, the people who publicly defined algorithm first in the year 1977.
The ECC
The Elliptic curve cryptography also referred to as the ECC usually depends on the algebraic structure of the elliptic curves over the finite fields. Generally, it is mostly assumed that by discovering discrete logarithms of the random elliptic curve component within the connection to publicly known base is somehow impractical.
Utilization of the elliptic curves in the cryptography was generally suggested by both Victor Miller and Neal Koblitz in the year 1985; though ECC algorithms entered into everyday use in the year 2004.
The benefit of using ECC algorithms over the RSA is that some of these keys could be somehow smaller, leading to improved security and speed. Drawback mostly lies in the notion that not all the applications and services are generally interoperable with the ECC-based SSL certificates.
The Pre-Shared Key Encryption Algorithms
The Pre-shared key encryption mostly utilizes some algorithms such as the Twofish, Blowfish or AES in creating the keys. The AES presently being the most famous. All such encryptions algorithms generally fall into block ciphers and stream ciphers. The stream ciphers usually apply the cryptographic key as well as the algorithm in every binary digit in the data stream, every bit each time. The block ciphers, on the other hand, apply the cryptographic key and the algorithm in blocking the data as a group. The block ciphers are usually the most popular symmetric encryption.
After review, we will like to see how available application & software will help to decrypt encrypted SSL/TLS.
Application & Software
There are numerous current inline approaches like the SSL application and proxies load balancers that offer SSL decryption, though they are not necessarily optimized for visibility architecture. These lack scalability in handling the traffic from many TAPs across networks or in filtering as well as replicating the decrypted to numerous monitoring tools. With such limited extensibility or modularity, increasing the SSL throughout regularly need fresh lastly, they offer no visibility responsibility, or traffic intelligence for the non-encrypted traffics.
They are also causing unadorned performance deprivation and are very expensive. Basically, offloading of the SSL decryption does not just permits the tools in returning to the full performance though they help in the elimination of some of the needs to enhance several decryption licenses for several tools.
I will like to share more about Gigamon (www.gigamon.com). It is a technology empowers users with universal control and visibility of the traffic across both virtual and physical environment with no impact on stability and performance of a production network. The decrypting SSL traffic needs the understanding of public keys utilized for encryption. Such is usually visible at the beginning of a transaction; access to private keys is mostly controlled by administrators.
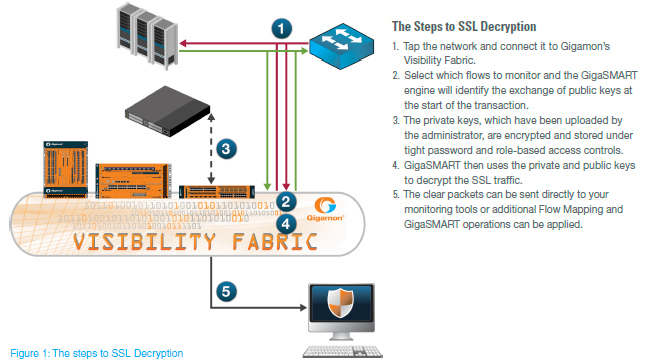
Specific security applications mostly do not assist with the other tools like application performance monitoring, since the Gigamon could merely supply the decrypted traffic to both concurrently.
Generally, by delivering the SSL decryption as universal service to connected security and monitoring tools, overall performance, security, and efficiency of infrastructure could be maximized. Further, provided that the Gigamon’s Visibility Fabric™ possesses some access to bidirectional traffic, this has the capacity of observing exchange of the public keys at the beginning of the transaction. Once administrators load private keys, they usually securely preserve them on the systems.
Appropriate handling of private keys is crucial for maintenance of security compliance. The Gigamon only permits the keys being uploaded, deleted or changed by the users designated by administrators. The keys are usually encrypted utilizing individual passwords that are unique from generic system administration passwords.
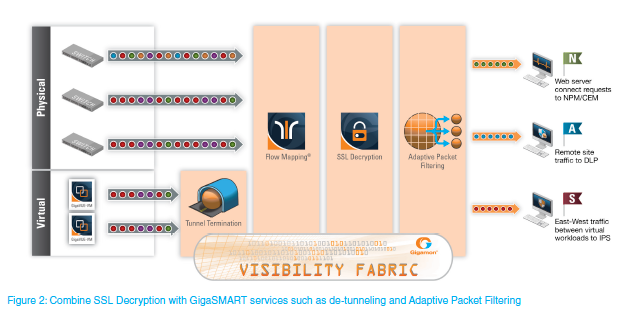
The SSL is a fundamental internet technique upon which quite a good number of applications would depend on. Nonetheless, it usually limits the visibility for both security and performance monitoring. Hence, growing security threat generally posed by the uninspected SSL sessions tends to increase the urgency for inspection of the SSL traffic.
Through decryption of the SSL traffic for the out-of-band monitoring of the Gigamon offers visibility where none was in existence. Instead of turning blind eyes to the SSL traffic, full abilities of the Flow Mapping, as well as the GigaSMART traffic intelligence, could be applicable. The decryption of the SSL is viewed to be an extremely processing procedure for the monitoring tools which do it themselves, which in turn significantly inhibits the tool’s performance as well as increases costs of the monitoring. Through the supply of clear and decrypted traffic to several tools, the Gigamon offers immediate returns and value on investments in the licensing fees, management costs and capital expenditure.
Aside from the apparent advantages, immediacy and efficiency of a CLI tool, I will like to take in how, http://www.wireshark.org/, Network Protocol Analyser, Wireshark works to decrypt SSL and TLS traffic.
It will decrypt the private key of appliance or servers within the PKCS#8 PEM format background.
Within the Wireshark, SSL dissectors are usually completely functional and tend to supports some advanced features like decryption of the SSL, in case encryption keys, are made available. Such is crucial while troubleshooting the Citrix products which utilize the TLS or SSL encryption. The procedure is as follows:
Procedure
Some of the requirements include:
The general knowledge as well as comprehension of:
- The Network Traces
- The certificates as well as utilization of the private and Public Keys
- Wireshark Network Protocol Analysers
- Networking, SSL/TLS as well as TCP/IP protocols
The Wireshark Setting
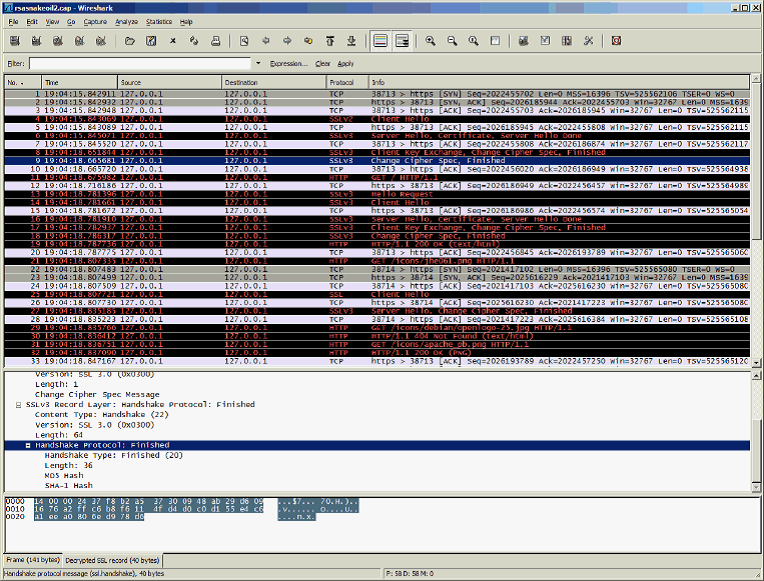
1. Start Wireshark and open the network capture (encrypted SSL should look like the screenshot below).
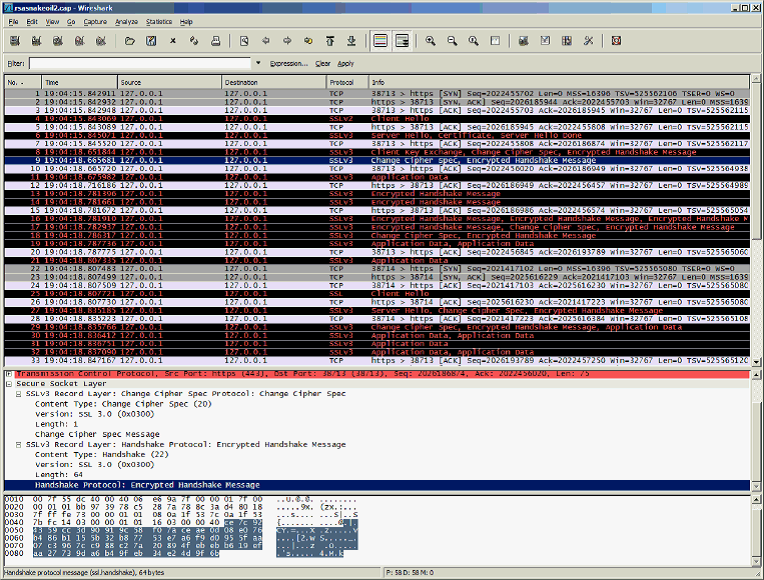
2. From the top menu select Edit > Preferences.
3. When the Preferences window opens, expand Protocols.
4. Scroll down and select SSL.
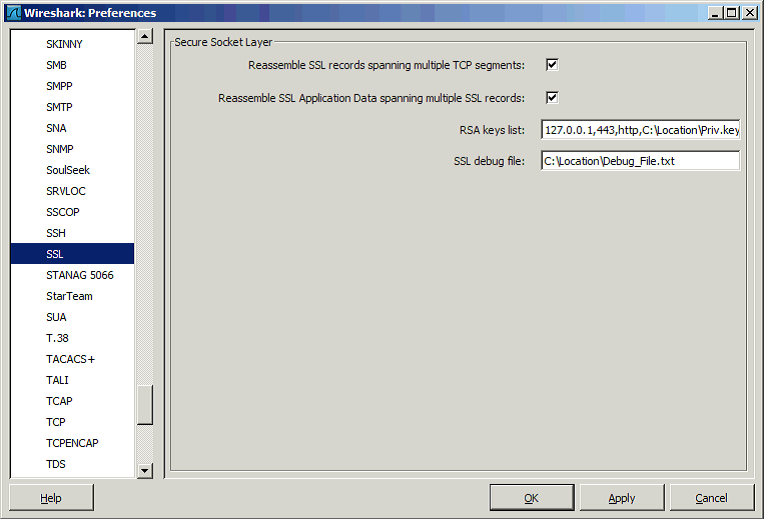
5. In the space labeled RSA keys list, provide the following information within the format <ip>,<port>,<protocol>,<key_file_name> also as shown in the above screenshot).
Where:
<ip> represents IP Address of appliance or server with private key
<port> represents 443 for the TLS or SSL
<protocol> represents the HTTP while
<key_file_name> represents location as well as file name of private key
Note: No spaces exist between the two colons. Additionally, utilizing the semicolons in separating entries, listing of the private keys could be utilized and entered for the decryption. “<ip>,<port>,<protocol>,<key_file_name>;<ip>,<port>,<protocol>,<key_file_name>;<ip>,<port>,<protocol>,<key_file_name>”
6. In the space labeled SSL debug file provide the file name as well as the location for the debug file.
7. Select OK
8. The SSL traffic should now be decrypted (decrypted SSL should look like the screenshot below).
Private Key Format
The Wireshark could be used in decrypting the SSL traffic so long the users have private keys. Generally, private key usually needs to be in decrypted PKCS#8 PEM format or the RSA format. This way, users could open as well as look in the critical files. In case it is in the binary format, this could be in DER format that could not be utilized with the Wireshark.
The primary users could utilize the Open SSL in converting the keys.
For instance, converting the PKCS#8 DER keys to the decrypted PKCS#8 PEM format, at $ prompt one should enter the following commands:
OpenSSL pkcs8 -nocrypt -in der.key -informat DER -out pem.key -out format PEM
Where:
The der.key represents file name as well as the path to DER key file
The pem.key represents file name as well as a path to PEM key file will
In this case, Decrypted PKCS#8 PEM format must look same to following:
Note that the key starts with:
-----BEGIN RSA PRIVATE KEY-----
In case it starts with:
-----BEGIN ENCRYPTED PRIVATE KEY-----
The key is then encrypted and calls for being decrypted with a right passphrase. One could utilize the OpenSSL in doing this.
1. First, at $ prompt, one should enter this command: OpenSSL RSA
In case one enters such command minus any arguments, one is impelled as: read RSA keys
2. Secondly, one should enter the file name that is to be decrypted. Then the user could enter OpenSSL RSA commands with some arguments in case the users understand file name of the private key as well as decrypted PEM file.
For instance, in the case file name of the private key is my rickey.pvk and file name of the decrypted key is the crucial out.pem, the command becomes:
To conclude, as IT Security teams start planning and preparing to deploy a solution for managing SSL/TLS traffic, it’s imperative to consider several critical factors in making this transition as smooth and non-disruptive as possible. Review the following for additional guidance:
Conclusion
We all know that SSL/TLS has become the universal standard for authenticating and encrypting communications between clients and servers. It is pervasive in today's enterprises and overgrown due to the rapid increase in the cloud, mobile and web applications. However, SSL poses a security threat by introducing "blind spot" which increases the risk of advanced malware penetrating an organization and possibly exfiltration proprietary data, without detection. Enterprises need a unique Encrypted Traffic Management solutions to resolve this dilemma and enable organizations to inspect, decrypted manage SSL traffic to eliminate this dangerous "blind spot," enhance the existing security infrastructure with new and complete visibility into all network traffic and preserve data privacy to maintain compliance.
Author: Tan Kian Hua, Ph.D. student at LIGS University
Bibliography
Chuan Ji, Oct 19, 2011, Tags: Android, Featured, Retrieved from https://seasonofcode.com
Shedden, P., Ruighaver, A.B., Ahmad, A., (2006) Risk Management Standards ‐ The Perception of Ease of Use.
Shedden, P, Scheepers, R., Smith, M., Ahmad, A. (2009) Towards a Knowledge Perspective in Information Security Risk Assessments
Tony Campbell, (2016, May) Chap 5&6 Practical Information Security Management - A Complete Guide to Planning and Implementation
Jim Swauger, Jim Hawke, Retrieved from http://www.binaryintel.com/services